Howto get a 1Q trunk across the air gap using Cisco wireless access points.
(note it actually IS hard to do)
(note it actually IS hard to do)
by ralph klimek VK3ZZC May-2014
these configs will permit you to construct a air bridge that can ferry a complete 1Q trunk across an air gap. It uses standard autonomous firmware, full wpa2 PSK encryption and will transport a defined set of vlans whilst providing full remote management of the bridges. You will have to purchase/get/find the autonomous firmware yourself as I cannot supply it due to legal peril. There are excellent Russian archives of firmwares , or you will have to find a friendly CCIE.
Due to the complexity of the configuration you must make a rational decision about precisely which vlans you want trunked. There is no known configuration options that just transports all of them without micromanagement. If you require this level of simplicity you must purchase a specific air-bridge product. Why cant I just increase the mtu to accomodate a 1Q trunk ? Tried that too, no good. It appears that the "wap" product firmware will arbitarily drop a 1Q tagged frame unless told otherwise. The more expensive "bridge" product may just forward a trunk without further ado , I cannot prove that as I do not have the "bridge" model available.
You must also configure the switch feeding your air bridging waps with some care so that your management vlan is egressed without its vlan tags, it must appear on the native (untagged) interface, normally it is vlan 1.
This config was proven to work on the Model 3602, version ap3g2-k9w7-tar.152-4.JB3a.tar , fiddling around may be required on other Cisco wap models.
The motivation for this project was the aquisition of leases to two adjoining biuldings in the city by Monash. As expected, there was a requirement that our clients in these co-joined biuldings have a network connection to each other. The floor spaces were separated by a one meter air gap and two 1/2 meter thicknesses of load bearing masonary. The cost of running a fibre link between these two leased sites was mind-bogglingly large. Boring a hole between two adjacent mult-story city biuldings was left out of my job description. So we "burned" a "hole" using this radio link.
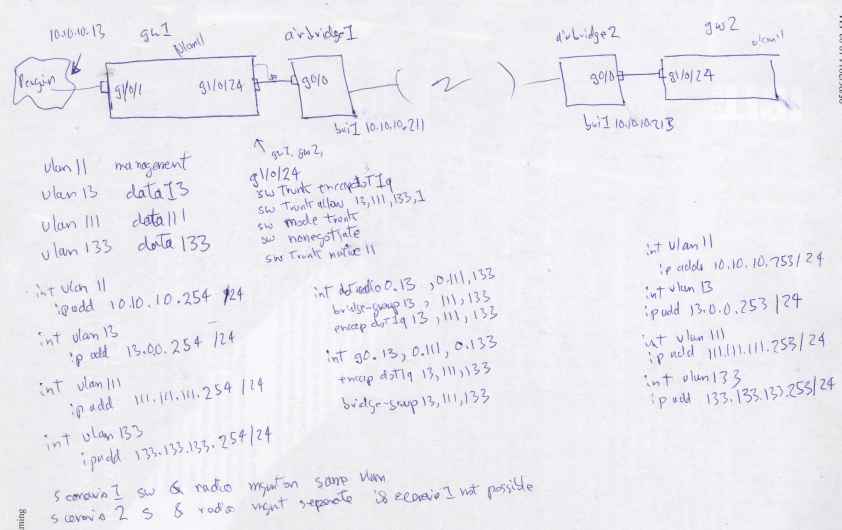
| I am implementing this scenario, two remote sites, I am wanting to send a 1Q trunk complete with switch and radio managmement and assorted production data vlans over an air gap |
 |
| bridge one, "near" bridge config | bridge one, "remote" bridge config | comments |
| ! ! Last configuration change at 04:39:59 UTC Fri Jun 22 2012 version 15.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname monash-college-near ! ! logging rate-limit console 9 enable secret 5 $1$ZbtD$amhH0VjhSfI. ! no aaa new-model no ip cef ip domain name ralphcor ! ! ! ! dot11 syslog ! dot11 ssid monash-collage-bridge1 vlan 1 authentication open authentication key-management wpa version 2 guest-mode infrastructure-ssid wpa-psk ascii 7 013E09your text here0A5A184581E58 ! ! dot11 guest ! ! ! username Cisco password 7 06250634F41 username ralphk password 7 0327210500 ! ! bridge irb ! ! ! interface Dot11Radio0 no ip address ! encryption mode ciphers aes-ccm ! encryption vlan 1 mode ciphers aes-ccm ! ssid monash-college-bridge1 ! antenna gain 0 stbc speed basic-1.0 basic-2.0 basic-5.5 basic-11.0 basic-6.0 basic-9.0 basic-12.0 basic-18.0 basic-24.0 basic-36.0 basic-48.0 basic-54.0 m0. m1. m2. m3. m4. m5. m6. m7. m8. m9. m10. m11. m12. m13. m14. m15. m16. m17. m18. m19. m20. m21. m22. m23. station-role root bridge ! interface Dot11Radio0.1 encapsulation dot1Q 1 native bridge-group 1 ! interface Dot11Radio0.13 encapsulation dot1Q 13 bridge-group 13 ! interface Dot11Radio0.111 encapsulation dot1Q 111 bridge-group 111 ! interface Dot11Radio0.133 encapsulation dot1Q 133 bridge-group 133 ! interface Dot11Radio1 no ip address shutdown antenna gain 4 peakdetect no dfs band block channel dfs station-role root bridge-group 1 bridge-group 1 subscriber-loop-control bridge-group 1 spanning-disabled bridge-group 1 block-unknown-source no bridge-group 1 source-learning no bridge-group 1 unicast-flooding ! interface GigabitEthernet0 no ip address duplex auto speed auto ! interface GigabitEthernet0.1 encapsulation dot1Q 1 native bridge-group 1 ! interface GigabitEthernet0.13 encapsulation dot1Q 13 bridge-group 13 ! interface GigabitEthernet0.111 encapsulation dot1Q 111 bridge-group 111 ! interface GigabitEthernet0.133 encapsulation dot1Q 133 bridge-group 133 ! interface BVI1 ip address 10.10.10.211 255.255.255.0 ipv6 address dhcp ipv6 address autoconfig ! ip forward-protocol nd ip http server no ip http secure-server ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag ! ! bridge 1 route ip ! ! ! line con 0 line vty 0 4 login local transport input all ! end | ! ! Last configuration change at 11:36:16 UTC Sat Jun 23 2012 version 15.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname monash-college-far ! ! logging rate-limit console 9 enable secret 5 $1$WmKE$uzv3mgqnGbzqilH101 ! no aaa new-model no ip cef ip domain name ralphcor ! ! ! ! dot11 syslog ! dot11 ssid monash-collage-bridge1 vlan 1 authentication open authentication key-management wpa version 2 guest-mode infrastructure-ssid wpa-psk ascii 7 013E0your text here5A180E21241E58 ! ! dot11 guest ! ! ! username Cisco password 7 080455D0A16 username ralphk password 7 00271A15754 ! ! bridge irb ! ! ! interface Dot11Radio0 no ip address ! encryption mode ciphers aes-ccm ! encryption vlan 1 mode ciphers aes-ccm ! ssid monash-college-bridge1 ! antenna gain 0 stbc station-role non-root ! interface Dot11Radio0.1 encapsulation dot1Q 1 native bridge-group 1 ! interface Dot11Radio0.13 encapsulation dot1Q 13 bridge-group 13 ! interface Dot11Radio0.111 encapsulation dot1Q 111 bridge-group 111 ! interface Dot11Radio0.133 encapsulation dot1Q 133 bridge-group 133 ! interface Dot11Radio0.666 encapsulation dot1Q 666 bridge-group 255 ! interface Dot11Radio1 no ip address shutdown antenna gain 0 peakdetect no dfs band block channel dfs station-role root bridge-group 1 bridge-group 1 subscriber-loop-control bridge-group 1 spanning-disabled bridge-group 1 block-unknown-source no bridge-group 1 source-learning no bridge-group 1 unicast-flooding ! interface GigabitEthernet0 no ip address duplex auto speed auto ! interface GigabitEthernet0.1 encapsulation dot1Q 1 native bridge-group 1 bridge-group 1 spanning-disabled ! interface GigabitEthernet0.13 encapsulation dot1Q 13 bridge-group 13 ! interface GigabitEthernet0.111 encapsulation dot1Q 111 bridge-group 111 ! interface GigabitEthernet0.133 encapsulation dot1Q 133 bridge-group 133 ! interface GigabitEthernet0.666 encapsulation dot1Q 666 bridge-group 255 ! interface BVI1 ip address 10.10.10.213 255.255.255.0 ipv6 address dhcp ipv6 address autoconfig ipv6 enable ! ip forward-protocol nd ip http server no ip http secure-server ip http help-path http://www.cisco.com/warp/public/779/smbiz/prodconfig/help/eag ! ! bridge 1 route ip ! ! line con 0 line vty 0 4 login local transport input all ! end | factory default boilerplare !give yourself a unique hostname set your own enable password set a unique ip domain name so that ssh will work after you create the keys send syslog messages, you have to supply the syslog server set your own unique infrastructure-ssid wap to wap authentication can only happen on Vlan1 use "open" standards compliant authentication tell the wap to use wpa2 probably redundant, you dont not actually need guest mode inform IOS that this wappage will only associate to another wappage set YOUR one pre shared session key probably redundant, you dont not actually need guest mode set your own usernames and session passwords enable bridging, its is in the boilerplate but if not, add it this is the tase config that tells the physcal radio interface how to use the encryption . It can only happen on the native vlan 1 bridge group this keyword cipher permits wpa2 ciphers aes-ccm is cisco speak for wpa2 assoicated this ciper method to an encryption process attached to vlan 1 associate the encrytpion method and cipher to an ssid (recall that a Cisco wap may present multiple ssids to the air interface I have no idea what stbc means, but it make this stuff work for wireless bridging one wap must be "root bridge" the peer wap must be "non root bridge" a radio subinterface must be configured for the native vlan 1 even though it exists be default on the physcial radio allready. We permit a vlan to egress the radio air interface by naming and configuring the subinterfaces. This bit is boiler plate and MUST be present or else the waps cannot associate Dot11Radio0.13 is the first production vlan to traverse the links you may invoke int Dot11radio0.anything you may invoke encapulation dot1Q anything bridge groups are only valid between <1-255> to you must manually and carfeilly manage your vlan to bridge group associattions this radio has another inbuild 5Ghz radio which will not be used this time the ethernet native interface requires allmost no config. Everything is done on the subinterfaces. this permits the native vlan 1 egress onto your 1Q trunk. It permits remote management of your air bridges. Bridge group 1 is not optional, you cannot reasign or reuse it for unauthorised purposes. The management is tied to interface BVI1 and also cannot be reassigned ! vlan 13 is a production traffic vlan vlan 111 is a production traffic vlan vlan 133 is a production traffic vlan vlan 666 is going nowhere ! There can be no bridge group 666 so we have to associate to some other bridge group number. in band management MUST go to BVI1 here. You cannot associate the console/management process to BVI13 or other. It just does not seem to work Here at work we also do IPV6. Why arent you ? I honestly do not know what ip forward-protocol nd means. It is part of the default IOS factory reset default factory config At monash we disable inbuilt web servers for security,but use only for inital setting up this tells the virutal bridge one to enable a TCPIP process set your own vty parameters. dont forget to set an access list for vty ports because you do not want the entire internet to manage YOUR bridge. dont forget to UNSHUT all your production interfaces. They may come up in shutdown state by default think of bridge groups as a collection of completely standalone virtual ethernet switches |
| config of nearby router 1Q trunk | config of far switch's 1Q trunk | comments |
| interface GigabitEthernet1/0/24 switchport trunk encapsulation dot1q switchport trunk native vlan 11 switchport trunk allowed vlan 11,13,111,133 switchport mode trunk switchport nonegotiate | interface GigabitEthernet1/0/24 switchport trunk encapsulation dot1q switchport trunk native vlan 11 switchport trunk allowed vlan 11,13,111,133 switchport mode trunk switchport nonegotiate | vlan 11 is my chosen "switch management" vlan so it goes on the wire as a native untagged. It still must be permitted on the egress list ! When I set mode trunk it will be a trunk no ifs/buts if I also set switchport nonegotiate . the other vlans are "production" vlans . Notice how vlan 11 on the switch and vlan 1 on the wap correctly talk to each other...because they are untagged ! |
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname test-gateway-two
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$4CuIWlPMOH1
!
username ralphk password 0 Cisco
!
!
no aaa new-model
switch 1 provision ws-c3750g-24ts
system mtu routing 1500
no ip domain-lookup
ip domain-name ralphcor
!
!
!
!
!
!
!
!
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface GigabitEthernet1/0/1
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/3
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/4
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/5
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/7
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/8
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/9
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/10
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/14
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/15
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/16
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/17
!
interface GigabitEthernet1/0/18
!
interface GigabitEthernet1/0/19
!
interface GigabitEthernet1/0/20
!
interface GigabitEthernet1/0/21
!
interface GigabitEthernet1/0/22
!
interface GigabitEthernet1/0/23
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 11,13,111,133
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/24
switchport trunk encapsulation dot1q
switchport trunk native vlan 11
switchport trunk allowed vlan 11,13,111,133
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface Vlan1
no ip address
!
interface Vlan11
ip address 10.10.10.253 255.255.255.0
!
interface Vlan13
ip address 13.0.0.253 255.255.255.0
!
interface Vlan111
ip address 111.111.111.253 255.255.255.0
!
interface Vlan133
ip address 133.133.133.253 255.255.255.0
!
ip classless
ip http server
ip http secure-server
!
!
!
!
!
line con 0
line vty 5 15
!
end
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname test-gateway-one
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$YDdD$LnaG.nfUdQeMqjd03aP30
!
username ralphk password 0 Cisco
!
!
no aaa new-model
switch 1 provision ws-c3750g-24ts
system mtu routing 1500
ip routing
no ip domain-lookup
ip domain-name ralphcor
!
!
!
!
crypto pki trustpoint TP-self-signed-4158367104
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4158367104
revocation-check none
rsakeypair TP-self-signed-4158367104
!
!
crypto pki certificate chain TP-self-signed-4158367104
certificate self-signed 01
B5B7BC68 9809D24A E5C33E86 D65E4415 86905623 256849CF 3C3FCEFF D26E4DDC
99BDBE9E 9BFB7A06 D1FD3F51 B4E9A934 B50E3EAA A551A957 0FDAE25E 41FFB7C0
7CC4CF47 F5ABA223 BC6E1021 44D8B826 7D155034 301FBFAA C7E8F1EC C72C33BF
D21F9566 1BE49A71 EBBF43B2 07
quit
!
!
!
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface GigabitEthernet1/0/1
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/3
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/4
switchport access vlan 11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/5
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/7
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/8
switchport access vlan 13
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/9
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/10
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport access vlan 111
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/14
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/15
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/16
switchport access vlan 133
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/17
!
interface GigabitEthernet1/0/18
!
interface GigabitEthernet1/0/19
!
interface GigabitEthernet1/0/20
!
interface GigabitEthernet1/0/21
!
interface GigabitEthernet1/0/22
!
interface GigabitEthernet1/0/23
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 11,13,111,133
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/24
switchport trunk encapsulation dot1q
switchport trunk native vlan 11
switchport trunk allowed vlan 11,13,111,133
switchport mode trunk
switchport nonegotiate
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface Vlan1
ip address 10.0.0.1 255.255.255.0
!
interface Vlan11
ip address 10.10.10.254 255.255.255.0
!
interface Vlan13
ip address 13.0.0.254 255.255.255.0
!
interface Vlan111
ip address 111.111.111.254 255.255.255.0
!
interface Vlan133
ip address 133.133.133.254 255.255.255.0
!
ip classless
ip http server
ip http secure-server
!
!
!
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
config notes
the platform here is a pair 3750 running routing ipservices images. This is used because I can assign ip address to each vlan interface. This scenario will not werk using only the ipbase images (they only permit a management vlan interface to be "UP")
preload the routers with their all there vlans, then create interfaces. Beware vlan interfaces do not come "up" untill they are associated with at lease one physical interface that is UP.
the 1Q trunk interfaces on port g1/0/23 was used to short circuit the air bridge to test that spanning tree was working properly. It is ! You may use this config to run extra parallel trunks for resilience ! We do pvrst+ at monash because it works extremely well.
the radio recieved signal strength indication RSSI can be read from the waps with the cli command. The signal strength in this example represents a test lab scenario where the waps are allmost touching ! In the real world you might expect -50 to -70 dbm for a good link, -80dbm for a marginal link.
monash-college-near#sho dot11 associations all | inc Signal
Signal Strength : -18 dBm Connected for : 975 seconds
Signal to Noise : 77 dB Activity Timeout : 30 seconds
monash-college-near#sho dot11 associations all | inc Signal
Signal Strength : -10 dBm Connected for : 978 seconds
Signal to Noise : 85 dB Activity Timeout : 30 seconds
monash-college-near#sho dot11 associations all | inc Signal
Signal Strength : -9 dBm Connected for : 1364 seconds
Signal to Noise : 86 dB Activity Timeout : 30 seconds
monash-college-near#